Cookies help us deliver our services. By using our services, you agree to our use of cookies.
Search
Welcome to ICT
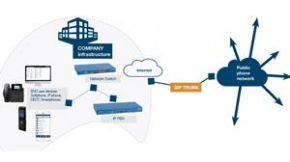
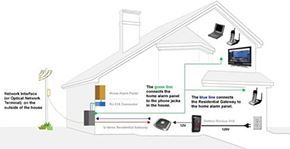
Since 1991, we have been delivering Product & Support Services for Information Communication Technology (ICT) platforms, including dependable Business Hosted PBX solutions, SIP Trunking and Hybrid Phone Systems. Serving South Western Ontario, we specialize in providing cutting-edge ICT solutions and business technology support, ensuring that your operations run smoothly and efficiently.
Our commitment is to offer professional ICT products & services tailored to your needs, utilizing proven technologies and best practices.
Featured
- Wireless Indoor
- IP Video Phone
- VoIP Headsets
- IP Phone Wired
Defining Value
Grandstream GRP2624 8-Line Professional Carrier-Grade IP Phone with Dual PoE Gigabit Ethernet Ports and Dual-band 2.4-GHz & 5-GHz Wi-Fi - Black
$130.38
Go To Product PageFeatured products
Mikrotik RBLHGGR&R11e-LTE6 kit
Mikrotik RBLHGGR&R11e-LTE6 kit. LHG LTE6 kit can connect to cell towers in extreme rural locations, giving you the ability to provide last mile internet access where nothing else is available.
$274.00
MikroTik MTAS-5G-15D120 mANT 15s Sector Antenna
MikroTik MTAS-5G-15D120 mANT 15s Sector Antenna
$74.56
Bestsellers
MikroTik RB960PGS hEX PoE Gigabit Router
5x Gigabit Ethernet with PoE output for four ports, SFP, USB, 800MHz CPU, 128MB RAM, RouterOS L4
From $115.32
X-lite 4.0: VoIP Softphone for MAC
The X-lite 4.0 Softphone is a downloadable virtual SIP phone that you can use on your computer to have connectivity no matter where you might be in the world.
$2.50
Foscam HD720P FI9816P(W) Indoor Wireless Night Vision PT (White) (Import)
Foscam HD720P FI9816P(W) Indoor Wireless Night Vision PT (White) (Import)
$224.95
UniFi6 Mesh AP WiFi 6
Ubiquiti UnFi AP WiFi 6 Mesh a high-performance, four-stream WiFi 6 access point that provides best-in-class signal meshing to enhance the wireless coverage of home and enterprise networks.
$298.00
New products
Ubiquiti UCG-ULTRA UniFi Cloud Gateway Ultra
Ubiquiti UCG-ULTRA Powerful and compact multi-WAN UniFi Cloud Gateway with a full suite of advanced routing and security features. Completely plug-and-play with no CloudKey required. Just add internet.
$205.43
Ubiquiti UCG-MAX UniFi Cloud Gateway Max
Ubiquiti UCG-MAX UniFi Cloud Gateway Max Compact 2.5G Cloud Gateway with 30+ UniFi device / 300+ client support, 1.5 Gbps IPS routing, and selectable NVR storage.
$414.00
Ubiquiti UX7 Unifi Express 7
Ubiquiti UX7 Unifi Express 7 Mesh-scalable, super-compact 10G Cloud Gateway with integrated Wi-Fi 7
$316.25
Yealink WH68UC WH68 Hybrid Microsoft Teams Wireless DECT Headset
Yealink WH68UC WH68 Hybrid Microsoft Teams Wireless DECT Headset
$263.36
Spring Deals!
HT812 VoIP SIP ATA / NAT Router, 2 x FXS, 1 x Gigabit Ethernet LAN, 1 x Gigabit Ethernet WAN, T.38 fax compliant, HD Audio.
$87.02
Go To Product Page