DDoS Extortion Attacks Against SIP/RTP VoIP Providers
High-Profile DDoS Extortion Attacks Against SIP/RTP VoIP Providers

ASERT Threat Summary
Date: October 22nd, 2021
Severity: Informational.
Distribution: TLP: WHITE
Categories: Availability
Contributors: Bill McDonough, Bill Cerveny, Tony Scheid.
Executive Summary
Beginning in September 2021, aggressive threat actors have targeted multiple Voice-over-IP (VoIP) communication providers with a campaign of high-impact DDoS extortion attacks. These attacks incorporate a range of UDP reflection/amplification and application-level DDoS attack vectors which have disrupted VoIP services for organizations unprepared to mitigate the attacks. In many cases, adversaries attempted to pressure targeted organizations into making crypto-currency extortion payments in exchange for ceasing the attacks. This Threat Summary includes recommendations for successfully mitigating these attacks.
Key Findings
- DDoS Extortion attacks against VoIP providers have resulted in outages and disruption to operations and services globally
- These attacks leverage well-known DDoS attack vectors which in many cases succeed in disrupting mission-critical services of unprepared VoIP operators
- Following Best Current Practices (BCPs), properly tuning network access control lists (ACLs), and ensuring critical systems/services are protected by modern Intelligent DDoS Mitigation Systems (IDMSes) empowers organizations to successfully defend against these attacks.
Description
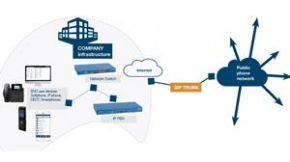
Beginning in September of 2021, multiple providers of Session Initiation Protocol (SIP)/Real-time Transport (RTP) VoIP services globally reported that their respective networks and service delivery infrastructures were being targeted by DDoS extortionists. In early October, the cadence of DDoS extortion attacks increased globally, with both wholesale and retail VoIP providers targeted
As is commonplace in DDoS extortion scenarios, demonstration DDoS attacks are launched against targeted operators, and emailed extortion demands are subsequently mailed to key personnel within those organizations; follow-up attacks are threatened if the extortion demands are not met. In most (but not all) cases, if the extortion demands are not met, threatened follow-up attacks do not occur, and the attacker moves on to other targets.
Multiple UDP reflection/amplification DDoS vectors are typically employed in these attacks, alongside direct-path SIP application-layer attacks. In some cases, suboptimal placement of stateful firewalls in front of SIP/RTP session border controllers (SBCs) and VoIP PBXes has negatively impacted the availability and resiliency of targeted SIP/RTP VoIP infrastructure, increasing the susceptibility of targeted service delivery elements to disruption by DDoS attacks. Similarly, the lack of situationally-appropriate network access control policies implemented via access-control lists (ACLs) on hardware-based routers and/or layer-3 switches has allowed attackers to negatively impact some SIP/RTP VoIP operators. These attacks utilized UDP reflection/amplification DDoS vectors to generate DDoS attack traffic which is clearly out of profile for VoIP services.
While in many cases emailed DDoS extortion demands are never viewed by their intended targets due to poor email address selection on the part of the attacker, it appears that over the course of this particular attack campaign, due diligence has generally been exercised in identifying email mailboxes which are likely to be actively monitored by targeted organizations.
Collateral Impact
Successful DDoS attacks against wholesalers of SIP/RTP VoIP services can significantly impact organizations which resell these services at the retail level. Disruption of SIP/RTP VoIP services retailed to end-customers such as enterprises, governmental entities, et. al. can result in the inability to deliver critical products and services, including emergency response, medical care, etc.
High-volume DDoS attacks can congest peering, transit, core, distribution, and access links, disrupting bystander internet traffic along with legitimate traffic destined for the intended target. Shared networking, computing, storage, and ancillary supporting infrastructure can be negatively impacted by high-volume DDoS attacks. These factors can result in significant collateral damage footprints.
The collateral impact of UDP reflection/amplification attacks is potentially quite high for organizations and individuals whose misconfigured servers/services are abused as reflectors/amplifiers. This may include partial or full interruption of mission-critical applications and services, as well as additional service disruption due to transit capacity consumption, state-table exhaustion of stateful firewalls and load-balancers, etc.
Mitigating Factors
DDoS attack traffic can be mitigated via the implementation of industry-standard best current practices (BCPs) such as situation appropriate network access control policies; network infrastructure-based reaction mechanisms such as flowspec; and intelligent DDoS mitigation systems (IDMSes) such as NETESCOUT Arbor Sightline/TMS and AED/APS.
Collateral impact to misconfigured, abusable servers/services leveraged as reflectors/amplifiers by attackers in order to launch DDoS attacks can motivate network operators and/or end-customers to remove or remediate affected systems.
Traceback of spoofed DDoS attack traffic to its ingress points by network operators and subsequent implementation of source-address validation (SAV) can prevent attackers from launching both reflection/amplification and spoofed direct-path DDoS attacks.
Recommended Actions
All relevant network infrastructure, architectural and operational BCPs should be implemented by SIP/RTP VoIP operators.
SIP/RTP VoIP operators should implement situation specific network access control policies via stateless ACLs on hardware-based routers and/or layer-3 switches. Wherever possible, stateful firewalls and/or load-balancers deployed northbound of SBCs and SIP/RTP PBXes should be removed; if these stateful devices cannot be immediately removed, they must be protected against DDoS attacks in the same manner as the SBCs and SIP/RTP PBXes sited behind them.
Protocols and ports used by different SIP/RTP VoIP services may vary considerably based upon operator configuration choices. Return traffic related to outbound SIP and RTP sessions generally requires reciprocal inbound network access control policy stanzas to be implemented. Whenever possible, network access control policies restricting access to SIP/RTP VoIP services should be implemented via situation specific network access control policies.
- It is imperative that SIP/RTP VoIP operators have a detailed understanding of the specific protocols and ports required by their service delivery infrastructure (and that of their customers/correspondents) in order to craft situation appropriate network access control policies and to provision relevant DDoS countermeasures.
DDoS defenses for all public-facing internet properties and supporting infrastructure should be implemented in a situation appropriate manner, including periodic testing to ensure that any changes to organization’s servers/services/applications are incorporated into its DDoS defense plan. Organic, on-site intelligent DDoS mitigation capabilities should be combined with cloud- or transit-based upstream DDoS mitigation services in order to ensure maximal responsiveness and flexibility during an attack.
Whenever possible, separate IP addresses should be used for receiving inbound SIP/RTP sessions and for initiating outbound SIP/RTP sessions. This practice facilitates the implementation of more granular network access control policies and DDoS countermeasure provisioning.
flowspec can be used by network operators to mitigate both UDP reflection/amplification DDoS attacks and SIP/RTP application-layer DDoS attacks. It is important to ensure that reaction access-control list (ACL) stanzas propagated via flowspec are configured in such a way to minimize the risk of overblocking.
Authoritative and recursive DNS services for SIP/RTP VoIP operators MUST be protected against DDoS attacks in order for VoIP services to function. AIF Templates providing examples DDoS countermeasure provisioning for DNS servers are available to AIF-entitled Sightline/TMS operators under the titles ‘DNS Recursive Server’ and ‘DNS Authoritative Server’, respectively.
It is imperative that organizations operating mission-critical public-facing Internet properties and/or infrastructure ensure that all servers/services/application/datastores/infrastructure elements are protected against DDoS attack, and are included in periodic, realistic tests of the organization’s DDoS mitigation plan. In many instances, we have encountered situations in which obvious elements such as public-facing Web servers were adequately protected, but authoritative DNS servers, application servers, and other critical service delivery elements were neglected, thus leaving them vulnerable to attack.
All potential DDoS attack mitigation measures described in this Summary MUST be tested and customized in a situation appropriate manner prior to deployment on production networks.
Finally, organizations must never pay DDoS extortionists, because they will continue to attack and demand larger payments, and other threat actors will learn of the payments and attack organizations known to have made extortion payments to attackers.